Time to Upgrade from SHA-1
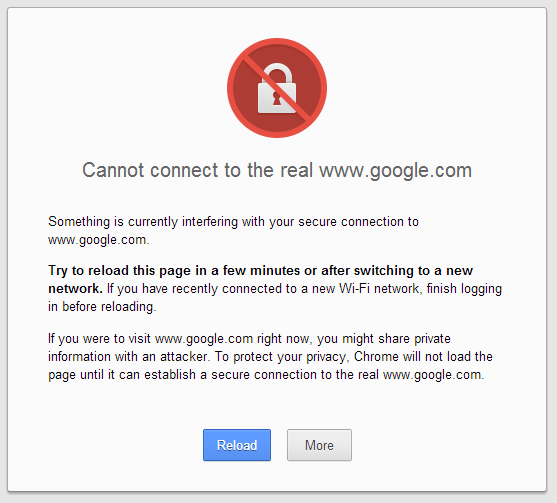
A potential client clicks on a link to your website. They get a warning that your security certificate may not be reliable. What would that do to the reputation around the integrity of your site?
That may be the fate for sites that use SHA-1 for their HTTPS connections and having not upgraded their certificates by January 1, 2017.
The phasing out of SHA-1 comes as no surprise. What wasn’t expected was the timing. Most experts believed that SHA-1 would remain an effective Hash algorithm for SSL certificate until 2018.
Earlier this year, researchers revealed the vulnerability to collision attacks already exists today. The expectation was that the computational power needed to find collisions in SHA-1 would remain prohibitively expensive for those with nefarious intentions. A successful collision attack is now possible on systems that cost $75,000 to $120,000. Even though there has not been a concrete example of a compromise “in the wild”, the threat becomes more immediate.
The Challenge of Outdated Browsers
The fact that not all browsers can handle SHA-2 creates an additional challenge for companies like Facebook. Most of those browsers are being used in developing countries, where other obstacles already stand in the way of accessing the Internet. Facebook is estimating that more than 37 million people will not be able access encrypted sites.
Their solution to continue to use SHA-1 certificates for people who depend on outdated browsers is being met with some controversy. Facebook is lobbying for an exception to the CA/Browser forum‘s official baseline requirements.
Investment in SHA-2 Required Today
The only recourse is to invest time and resources into upgrading all certificates for secure browser communications to SHA-2.
The process to transition is rather complex. The best solution is to begin the process sooner rather than later or face the added expense of having to rush the project and risk introducing errors and issues.
The most difficult aspect of the transition will be in understanding the devices and applications that will or won’t work with SHA-2.
Prepare for SHA-3 for the Not so Distant Future
The demise of SHA-1 teaches us that we will need to prepare for the eventual replacement of SHA-2. As organizations move to SHA-2, it’s a good idea to document the processes and lessons learned so they can be applied in the future.
Although it’s tempting to consider leap-frogging to SHA-3, it is too early to move to SHA-3 at this point in time, as the new hash will not be ready for global adoption for another five years.
Working with a Partner You Can Trust
The transition from SHA-1 to SHA-2 will require investment. Hiring a security firm to manage the process and ensure the work is done expertly will be the right approach for most organizations. At the very least, you may want to hire out to audit your implementation of your upgrade to SHA-2.
The key is to find a firm that has a reputation for doing expert work and can back up their promises with experience. If this isn’t your area of expertise, don’t hesitate to ask for a comprehensive quote, details about contingency plans for any hiccups, and references.
They should also be able to provide a time line and regular status updates on how the project is progressing. A significant part of this type of undertaking is ensuring the project is managed properly for success.
