Time to Upgrade from SHA-1
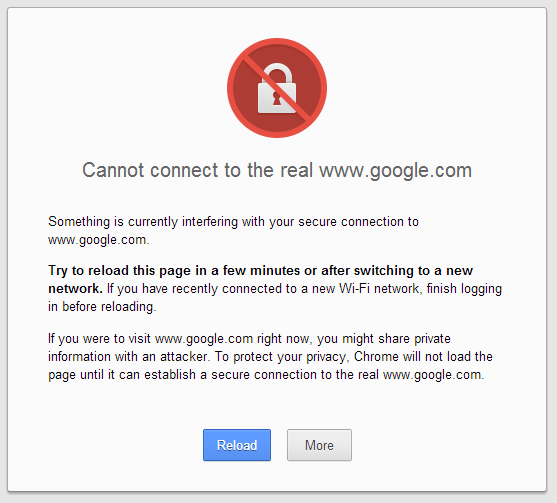
A potential client clicks on a link to your website. They get a warning that your security certificate may not be reliable. What would that do to the …
How Smart Cars Will Make Roads Safer
According to the United States Department of Transportation’s National Center for Statistics and Analysis, 2.4 million vehicle-related injuries occurred …
How To Get Signatures On Smaller NFC Tags
BlackSeal currently requires NFC tags with about 500 bytes of memory available to be able to fit a URL plus a signature on the tag. But is it possible …
Cryptography in Transition: Leaving Behind Human Oversight
Cryptography has primarily existed to send secret messages, often political or military, between people. For the political case I’m reminded of the …
Implicit Certificates in V2V
There has been a lot of news recently about vehicle-to-vehicle or “V2V” technology and how it is being adopted by the U.S. Department of Transportation …
Implicit Certificates vs. Conventional Certificates
As devices proliferate and become more mobile, managing relationships between them is critical. Devices will move in and out of range of each other and …
Machine-to-Machine (M2M) Certificates Versus Traditional Certificates
Conceptually there is little difference between traditional certificates and new M2M certificates; both are intended to authenticate identities via a …
Secure Authentication
In the last few years Machine-to-Machine (M2M) has seen widespread use and can be found in a variety of applications within the Internet of Things …
Digital Certificates
A digital certificate is an electronic credential used to verify and authenticate the identity of an individual or device. Its primary function is to …
