LoRaWAN Security Overview

Low Power Wide Area Networks (LPWANs) are emerging to address Internet of Things applications where devices are distributed over a wide area. Think …

Low Power Wide Area Networks (LPWANs) are emerging to address Internet of Things applications where devices are distributed over a wide area. Think …

As keyless entry systems become ubiquitous, concerns about security are growing and gaining attention. Key sharing is one area that continues to present unique and significant challenges for car owners and manufacturers alike. …

October IoT Roundup: DDoS Predictions Fulfilled, We Look to Medical Devices Next …

Hearing Aid technology has evolved tremendously in the last 20 years. I bought my first hearing aids in 1996, and …
The Internet of Things is poised to become an enormous $11 trillion-dollar industry, if it doesn’t become a liability for enterprises and …

Speaking at the Security of Things forum in Cambridge, Robert Silvers of Homeland Security made a strong case for securing ourselves now instead of …
Would you feel comfortable riding in a driverless car? Groups that identify as The New America Foundation and Public Knowledge requested an emergency …

DEF CON held its 24th convention this August, highlighting the ever-growing cost of implementing security as an afterthought—and new executive survey data shows that security is becoming the number-one technological priority for businesses. …

This summer I have been lucky enough to work for TrustPoint Innovation as a co-op student. Since I am a math and computer science student at the University of Waterloo, with an interest in cryptography and information security, I couldn’t have asked for a better opportunity. …
Would you buy a house that anyone could access for $40? Volkswagen owners weren’t given the chance to consider this question when they bought their cars over the last two decades, according to Wired. …

It seems that many people have a blind faith when it comes to their devices. What will it take to get people to take IoT security seriously? …
Now that the term Internet of Things has taken root in our everyday vocabulary, Smart Cities is the next concept that’s bound to get a lot of attention. …

Whether we purchase devices on our own or just venture out into the world, the Internet of Things will have an impact on our lives. In many ways, these devices will improve how we run our cities …
Depending on the application, NFC/RFID tags may or may not require some level of security. If you were only interested in tracking assets, a simple serial number …
Who says the summer months are quiet? This June, there’s a lot of action in the automotive world, and TrustPoint Innovation is in the center of it all. …

The Internet of Things is expected to grow dramatically in just a few short years. According to a recent report by Gartner Group, we can expect to see 21 billion connected devices by 2020. The market value …
Earlier this month, TrustPoint Innovation presented at ITS Canada’s 2016 conference. We provided an update on the Security Credential Management System (SCMS), the security infrastructure that powers the US Department of Transportation’s …

IoT security issues are becoming more and more common. Every new survey seems to reveal that consumers are wary about the connected …
If you haven’t seen the YouTube video of the 70-year-old woman behind the wheel of a self-driving Tesla, take a look. She’s clearly not ready for …
NFC is a great technology. It allows us to easily access and share information. Its functionality is perfect for our smartphone-connected world. At …

The issues with IoT security are so widespread that most articles that focus on how the Internet of Things will change our lives also give attention …

A couple of months ago, Volvo unveiled their new keyless entry system at MWC 2016. Like many other manufacturers, Volvo is looking at taking advantage …
The battle over an encrypted iPhone raging between Apple and the FBI is both complicated and simple. It goes beyond unlocking the phones for suspected …

The promise of a connected world offers so many opportunities to make life easier. However, developers need to get their act together when it comes to …
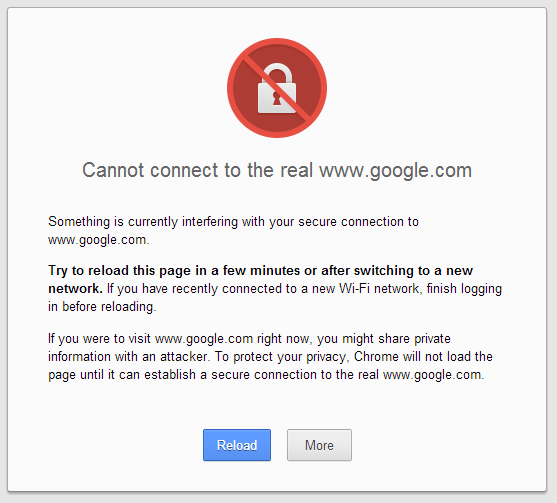
A potential client clicks on a link to your website. They get a warning that your security certificate may not be reliable. What would that do to the …
IoT is making a lot of waves — with promises of more and more connected devices coming out over the next 10 years. With the number of stories …
Another CES is in the books. As usual, the booths were crammed with exciting innovation. It’s been fascinating to watch the evolution of CES over the …
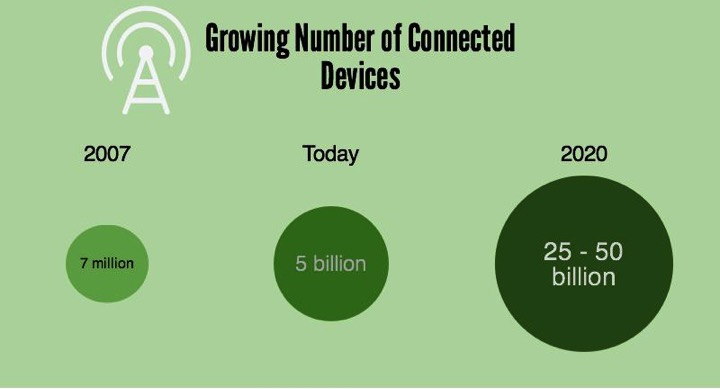
Connected devices are now a part of everyday life. While not everyone may fully understand the exact definition of “the Internet of Things”, the term …
The NAIAS in Detroit, Michigan is the largest car show in the world. Just a month away, the show promises to unveil the latest models and the newest …
Devices that connect to the Internet are susceptible to hacking. The latest security breach came out this week as VTech confirmed that the data of …
We use doors every day to gain access to our homes, cars and offices. While lock and key mechanisms have evolved significantly, a certain lack of …
After surviving a harrowing experience at the wheel of a hacked vehicle, WIRED journalist Andy Greenberg shared his insight in to what can be …
Near Field Communication, Internet of Things and Vehicle-to-Vehicle — these are all emerging technologies that promise to improve our lives. Without …

Ontario is the first province in Canada to remove restrictions that will allow for testing driverless vehicles on provincial roads and highways …
So often when we discuss the Internet of Things, automated machines, and integrating the Internet into every facet of our everyday lives, we focus …
We know manufacturers care about counterfeits. High quality counterfeits compete directly with the genuine article leading to lost sales. Low …
As more and more household products are developed with Internet integration in mind, the shift towards an all-connected “Internet of Things” …
In another major shift for IoT development, news broke recently that IBM has signed a deal with ARM Holdings, a British company that designs …
If you’ve bought a car manufactured in the past few years, chances are high that it will utilize between 20 and 70 computers, all with their own …
The IC3 (Internet Crime Complaint Center), a division of the FBI, released a public service announcement on September 11, 2015, regarding …

The Internet of Things. Five years ago very few people had heard of the concept. Despite the fact that the term is now commonly used …
From June 15–19, 2015, sixteen connected-car companies from Canada travelled to Silicon Valley near San Francisco to meet with the top automotive …
Taylor Swift has long held a passionate stance on the protection of intellectual property in the music industry, and is not afraid to stand up for …
As our world becomes more entwined with the internet, we risk laying bare our personal lives for the world. This isn’t some futuristic fear either; we …
Driving down a highway in your new vehicle, there would be nothing more terrifying than to cross paths with a careless driver or unavoidable obstacle …
The options for using NFC tags in advertising are endless. NFC (or near field communication) is a wireless technology that facilitates fast and efficient …
Government officials need their electronic devices to be secure. Blackberry security has recently come under scrutiny from Shafiq Qaadri, a Liberal MPP …
According to the United States Department of Transportation’s National Center for Statistics and Analysis, 2.4 million vehicle-related injuries occurred …
What if your most intimate secrets were exposed to the world? The possibility of health care privacy breaches in the new era of the Internet of Things …
Are government agencies keeping up with technological advancements? The expansion of the Internet of Things (IoT) has created numerous possibilities for …
Consumers search online for authentic products at the very best prices. Unfortunately, they have no way to tell if they are purchasing a knockoff. …
In cryptography, a side channel attack accesses information about a secured system through the analysis of physical attributes of the system. This is in …
Technology can make life simpler and easier. But you need to know how to use it properly; otherwise, the potential dangers technology can pose are real …
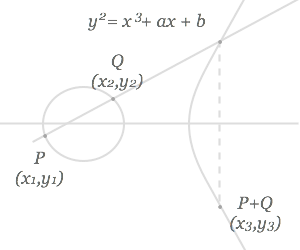
Cryptography has primarily existed to send secret messages, often political or military, between people. For the political case I’m reminded of the …
IKEA has a newfound set of ideas for their version of the Kitchen of 2025. They call this vision the “Concept Kitchen”, and have recently shared their …
The Internet of Things is here to stay. There will only be more devices, not less, that are connecting to your network in the future. Unfortunately, the …
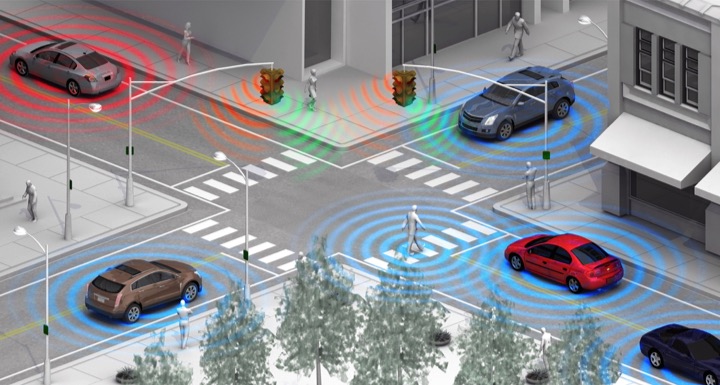
There has been a lot of news recently about vehicle-to-vehicle or “V2V” technology and how it is being adopted by the U.S. Department of Transportation …
In mid-July of this year, President Obama was speaking at a federal highway research facility in Northern Virginia about the development and testing of …
NFC security is highly dependant on the targeted application and mode of operation. This post explores the three modes of NFC: Tag Reader/Writer, Card …
This question was posted a few years ago by Eric Vétillard in this blog post.
Recent articles appearing in The New York Times, Der Speigel, Canada’s The Globe and Mail, Britain’s The Guardian and a host of other media have …
A digital certificate is an electronic credential used to verify and authenticate the identity of an individual or device. Its primary function is to …
TrustPoint Innovation is bringing to the market a solution specifically designed to provide users and devices connected to M2M end points the ability to securely …